| Currently, this is a draft work-in-progress page. |
Contents
- 1 Introduction
- 2 Requirements
- 3 Overview
- 4 Install pre-requisite rpms
- 5 Prepare the ISO image
- 6 Create a directory in your Downloads for the ISO and configuration files
- 7 Make a working copy from the example for drakiso
- 8 Update drakiso configuration files to enable LUKS encryption processing
- 9 Add updated mgalive-root.sh (supporting LUKS)
- 10 Build the ISO using draklive2
- 11 Use isodumper to write the ISO to USB
- 12 Using the LUKS encrypted Mageia live persistent data USB
- 13 First use: steps to take when booted up from USB memory stick
- 14 Appendix-1: modified mgalive-root.sh with LUKS support
Introduction
This note describes how to create an encrypted live persistent USB memory stick with Mageia 7.
Requirements
For practical purposes, use the highest speed (eg USB 3.1 or higher) with enough space. It is possible to use as small at 16gb but that leaves very little space for anything useful.
In the example below we use a 128gb ADATA S102.
It also helps greatly if the computer where the USB stick is to be used has fast (USB 3 or higher) USB socket. The computer needs to be configured to allow booting from USB.
On HP systems, for example, on switching on one needs to repeatedly tap on the ESC(ape) key then when presented with the menu pres f9 to choose the bootable device and select the USB.
Overview
- preparations: install needed packages
- disk space requirements
- modify configuration settings for building the ISO using drakelive2
- Include mgalive-root.sh modified for LUKS (encryption support)
- Build the ISO using draklive2
- Plug in and identify the USB stick device name
- Run isodumper and select configuration: use persistent storage, enable encryption, provide eecryption key
- On receiving confirmation of isodumper completion, test booting with USB
Install pre-requisite rpms
urpmi drakiso drakiso-bootloader-files drakiso-null-bootloader x11-server-xephyr
Prepare the ISO image
ref: https://wiki.mageia.org/en/Draklive2#Quickstart see example 2
Need between 10 and 20 gb free space.
Create a directory in your Downloads for the ISO and configuration files
my_iso=~/Downloads/drakiso/my_iso/
mkdir -p ${my_iso}
Make a working copy from the example for drakiso
cp -r /usr/share/drakiso/examples/gui/ ${my_iso}
Update drakiso configuration files to enable LUKS encryption processing
cd ${my_iso}/gui/
Update file: config/build.cfg
Add the following:
# Support for encrypted persistent partition.
[ 'files/mgalive-root.sh', '/lib/dracut/modules.d/90mgalive/mgalive-root.sh', { mode => 755 } ],
below:
# Fix for sometimes wrong permissions after install.
[ 'files/draklive-install.d/run.d/home-live-permissions.sh', '/etc/draklive-install.d/run.d/home-live-permissions.sh', { mode => 755 } ],
so it looks like:
# Fix for sometimes wrong permissions after install.
[ 'files/draklive-install.d/run.d/home-live-permissions.sh', '/etc/draklive-install.d/run.d/home-live-permissions.sh', { mode => 755 } ],
# Support for encrypted persistent partition.
[ 'files/mgalive-root.sh', '/lib/dracut/modules.d/90mgalive/mgalive-root.sh', { mode => 755 } ],
],
remove_files => [
Update file: files/dracut-live.conf
change:
omit_dracutmodules+=" caps crypt dm dmraid mdraid lvm nfs i18n resume modsign "
to:
##omit_dracutmodules+=" caps crypt dm dmraid mdraid lvm nfs i18n resume modsign " omit_dracutmodules+=" caps dmraid mdraid lvm nfs i18n resume modsign "
Update file: config/settings.cfg
Be aware that if you decide to add:
region all
Then the resulting ISO will be huge. It is probably more practical to avoid using "region all" in config/settings.cfg
change:
desktop=Custom
to:
desktop=MATE_LUKS
Note that this desktop name will show up at the top of the grub splash screen on booting. I prefer the MATE desktop environment. Hence I used "MATE". The "_LUKS" is to remind the user that USB is LUKs encrypted.
Set the correct value for your system arch(itecture): 64 or 32 bit: change:
arch=
to (for example 64 bit):
arch=x86_64
Set correct correct value for your Mageia repository mirror. Example:
repository=http://mirrors.kernel.org/mageia/distrib/7
So, after editing config/settings.cfg should look something like:
vendor=Custom distro=Mageia product=Live desktop=MATE_LUKS release=7 arch=x86_64 repository=http://mirrors.kernel.org/mageia/distrib/7 workdir=
Add updated mgalive-root.sh (supporting LUKS)
Copy modified version of mgalive-root.sh (see Appendix-1, below) to ${my_iso}/gui/files/mgalive-root.sh.
Reference: Mageia enhancement bug request #24777, comment 16
Build the ISO using draklive2
This can take a long time: perhaps an hour or two. (May be faster if your "repository" is on your local file system.)
Note that we run this as non-root. At some point draklive2 will prompt for password if it needs to sudo. For this reason, you should install and configure sudo (see: configuring sudo for details).
cd ${my_iso}/gui/
draklive2 --clean --all
Example:
[mpb@zbook my_iso]$ pwd
/home/mpb/Downloads/drakiso/my_iso/gui
[mpb@zbook gui]$ draklive2 --clean --all
Using /home/mpb/Downloads/drakiso/my_iso/gui as directory root
Loaded /home/mpb/Downloads/drakiso/my_iso/gui/config/build.cfg as config file
* entering step "clean"
* step "clean" done
* entering step "root"
Installing Live system
Ignore the following Glib::Object::Introspection & Gtk3 warnings
Too late to run INIT block at /usr/lib64/perl5/vendor_perl/Glib/Object/Introspection.pm line 257.
Subroutine Gtk3::main redefined at /usr/share/perl5/vendor_perl/Gtk3.pm line 525.
MESA-LOADER: failed to open swrast (search paths /usr/lib64/dri)
libGL error: failed to load driver: swrast
Entering step `Language'
Entering step `License'
Entering step `Mouse'
Entering step `Hard drive detection'
Entering step `Installation class'
Entering step `Keyboard'
Entering step `Security'
Entering step `Partitioning'
Partition 3 does not start on physical sector boundary.
Partition 5 does not start on physical sector boundary.
Partition 6 does not start on physical sector boundary.
Partition 7 does not start on physical sector boundary.
Partition 8 does not start on physical sector boundary.
Partition 9 does not start on physical sector boundary.
Partition 3 does not start on physical sector boundary.
Partition 5 does not start on physical sector boundary.
Partition 6 does not start on physical sector boundary.
Partition 7 does not start on physical sector boundary.
Partition 8 does not start on physical sector boundary.
Partition 9 does not start on physical sector boundary.
Entering step `Formatting'
Entering step `Choosing packages'
warning: Generating 18 missing index(es), please wait...
GLib-CRITICAL **: Source ID 1328 was not found when attempting to remove it at /usr/lib/libDrakX/interactive/gtk.pm line 924.
Entering step `Installing'
sh: 1: rpm: not found
warning: /etc/resolv.conf created as /etc/resolv.conf.rpmnew
warning: /etc/rpm/macros created as /etc/rpm/macros.rpmnew
GLib-CRITICAL **: Source ID 1810 was not found when attempting to remove it at /usr/lib/libDrakX/interactive/gtk.pm line 924.
Running in chroot, ignoring request.
1/1: removing iwlwifi-firmware-20191220-1.mga7.nonfree.noarch
############################################################################################################################################################
Entering step `Users'
Entering step `Networking'
SIOCETHTOOL: Operation not supported
SIOCETHTOOL: Operation not supported
SIOCETHTOOL: Operation not supported
SIOCETHTOOL: Operation not supported
Entering step `Bootloader'
Entering step `Configure X'
Entering step `Summary'
Entering step `Services'
Entering step `Updates'
Entering step `Exit'
Partition 3 does not start on physical sector boundary.
Partition 5 does not start on physical sector boundary.
Partition 6 does not start on physical sector boundary.
Partition 7 does not start on physical sector boundary.
Partition 8 does not start on physical sector boundary.
Partition 9 does not start on physical sector boundary.
[sudo] password for mpb:
Customising Live system
* step "root" done
* entering step "boot"
Using kernel 5.4.12-desktop-1.mga7
Creating: target|kernel|dracut args|basicmodules
/boot/initrd-5.4.12-desktop-1.mga7.img|5.4.12-desktop-1.mga7| -f|
mkfs.fat 4.1 (2017-01-24)
* step "boot" done
* entering step "loop"
Have to process 4643 MB
Unrecognised xattr prefix system.posix_acl_default
Unrecognised xattr prefix system.posix_acl_access
* step "loop" done
* entering step "master"
GNU xorriso 1.5.0 : RockRidge filesystem manipulator, libburnia project.
Created ISO /home/mpb/Downloads/drakiso/my_iso/gui/Mageia-7-Live-Mate_LUKS-x86_64/dist/Mageia-7-Live-Mate_LUKS-x86_64.iso
* step "master" done
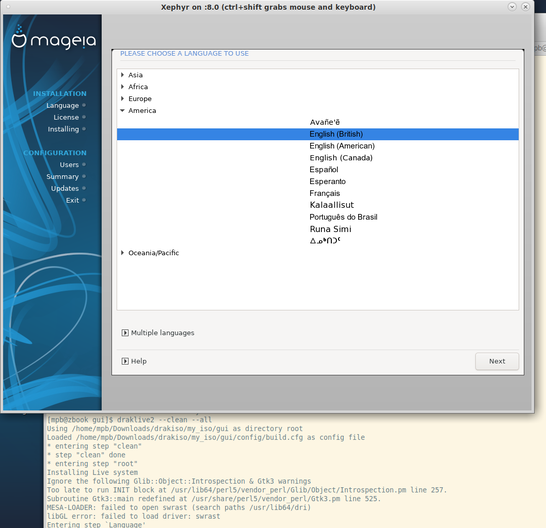
|
Example screen shot of running drakiso
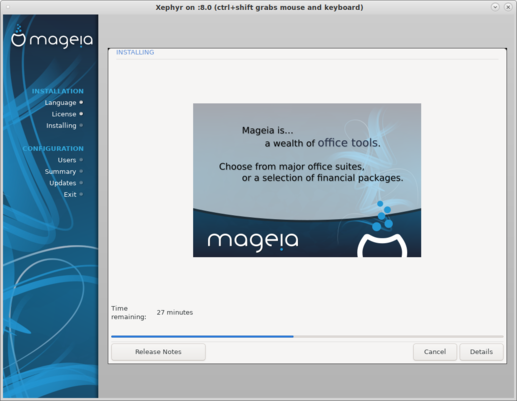
|
Example screen shot of running drakiso: doing the install process to ISO image.
Determine memory_stick_device name
In most systems, there will be a single disk drive which will have the reference /dev/sda. So, the when the USB memory stick is plugged in it will be: /dev/sdb.
memory_stick_device=/dev/sdb
We can also check and confirm the correct device name for the USB memory stick as follows:
- In a terminal, type:
journalctl -fa #Display system log (dynamically updated)
- Plug in the USB
- Observe the system log (from step 1, above) to see the device name for the memory stick. Example:
Dec 12 16:19:17 localhost kernel: sd 7:0:0:0: [sdc] 4016128 512-byte logical blocks: (2.06 GB/1.92 GiB)
Here, the device name is sdc, so we would use: memory_stick_device=/dev/sdc
Use isodumper to write the ISO to USB
Before starting isodumper, plug in the USB memory stick to be used and note the device name.
The version of isodumper described here can be found via: Comment 21 on bug report 24777.
Start isodumper via the graphical user interface (GUI) or from the command line (CLI).
Via GUI:
Applications -> Tools -> System Tools -> IsoDumper (GTK)
From command line:
/bin/sudo /usr/bin/isodumper
Note: as always when running a command that prompts for a password or key, use the full pathname to improve security.
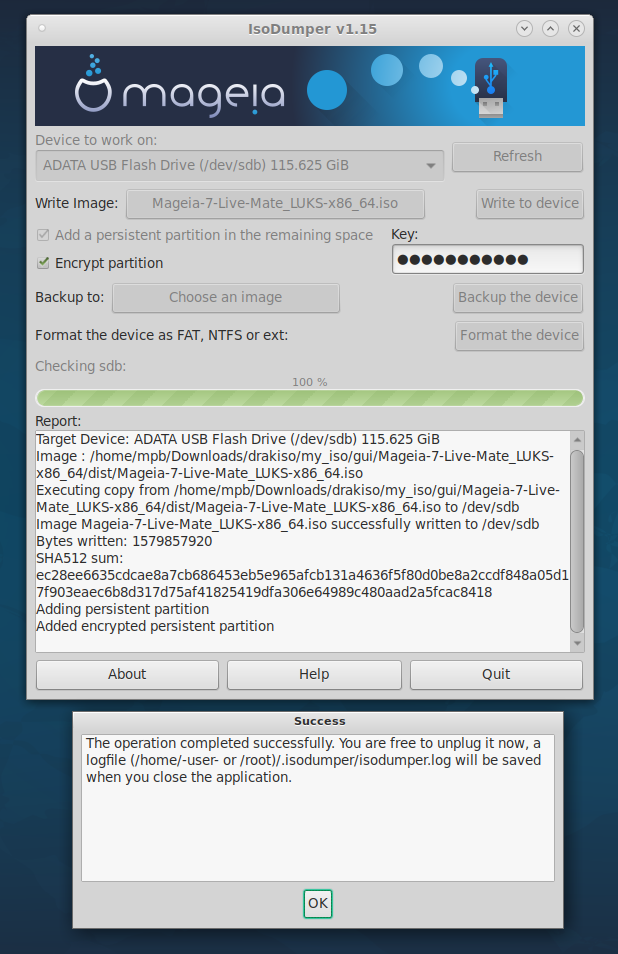
|
Example screen shot of running isodumper with options for persistence and encryption.
Using the LUKS encrypted Mageia live persistent data USB
Steps:
- Plug the USB memory stick in highest speed USB port on computer
- Power up (or reboot) computer and tap ESC escape key during start to enable choice of boot device
- On HP systems: F9 key will select boot options menu
- Identify and select USB device to boot with
- When prompted, enter the encryption pass phrase you used to encrypt
- After startup and login, note the output from df to confirm encrypted 3rd partition is union mounted. You will see "overlay" and the size.
Example: showing the overlay in output from df command:
[user@localhost ~]$ df Filesystem Size Used Avail Use% Mounted on devtmpfs 16G 0 16G 0% /dev tmpfs 16G 242M 16G 2% /dev/shm tmpfs 16G 1.3M 16G 1% /run /dev/loop0 1.5G 1.5G 0 100% /run/mgalive/ovlsize overlay 112G 1.5G 105G 2% / tmpfs 16G 0 16G 0% /sys/fs/cgroup tmpfs 16G 3.6M 16G 1% /tmp tmpfs 3.2G 56K 3.2G 1% /run/user/1000
Note: The read-only first partition which is the ISO image created at the start is showing here as:
/dev/loop0 1.5G 1.5G 0 100% /run/mgalive/ovlsize
the encrypted persistent 3rd partition showing here as:
overlay 112G 1.5G 105G 2% /
This is a union mount of the 1st and 3rd partitions. Any changes or updates are saved in the encrypted 3rd partition "overlay".
We can also display partition details on the USB with:
lsblk -f /dev/sda
Or:
lsblk -o NAME,FSTYPE,LABEL,UUID /dev/sda
Example:
[user@localhost ~]$ lsblk -o NAME,FSTYPE,LABEL,UUID /dev/sda NAME FSTYPE LABEL UUID sda iso9660 Mageia-7-Live-Mate_LUKS-x86_64 2020-01-23-00-01-22-00 ├─sda1 iso9660 Mageia-7-Live-Mate_LUKS-x86_64 2020-01-23-00-01-22-00 ├─sda2 vfat MGALIVE-ESP 1459-4A6B └─sda3 crypto_LUKS Mageia-7-Live-Mate_LUKS-x86_64 d99dd635-e4c9-448f-b007-a01c617b7d99 └─crypt_sda3 ext4 mgalive-persist 36d4932d-102d-4282-b42d-0055bff4af91
First use: steps to take when booted up from USB memory stick
Depending on the ISO that was created, there is probably a no-password login for user live. You probably need to create a new login and password for your own use then remove (or password protect) the live account.
You should also set a root password.
After checking you have network connectivity define urpmi sources and apply pending system updates.
Step 1: Security
First check security: make sure you create your own login account and add it to the wheel group (to enable you to sudo). Check for any accounts such as live which may have no password are either removed or password protected. Ensure you have a secure password on the root account.
Example: Create login and set password
In this example, change mylogin (below) to your preferred login account name. Note the use of "-G wheel". This is to enable the account to use sudo. Refer to Configuring_sudo for details on configuring sudo.
[live@localhost ~]$ /bin/su -c "/sbin/useradd -m mylogin -G wheel -s /bin/bash" [live@localhost ~]$ /bin/su -c "/usr/bin/passwd mylogin" Changing password for user mylogin. New password: Retype new password: passwd: all authentication tokens updated successfully.
Step 2: Disable updating of the mgalive-root.sh file
Recall that we used a modified for LUKS version of mgalive-root.sh.
If this was changed by system update to a version that does not support LUKS then we would lose access to the encrypted persistent 3rd partiton on the USB. To prevent this we can exclude the RPM package containing "mgalive-root.sh" from being updated (eg when "urpmi --auto-update" is run). First, find the full pathname for mgalive-root.sh:
[user@localhost ~]$ locate mgalive-root.sh /usr/lib/dracut/modules.d/90mgalive/mgalive-root.sh
Next, determine the package that /usr/lib/dracut/modules.d/90mgalive/mgalive-root.sh is part of:
[user@localhost ~]$ rpm -q --whatprovides /usr/lib/dracut/modules.d/90mgalive/mgalive-root.sh dracut-046-11.mga7
So the RPM package we need to exclude from updates is: dracut-046-11.mga7
We can add dracut to the URPMI exclusion list in: /etc/urpmi/skip.list:
echo "/^dracut/" >> /etc/urpmi/skip.list
Example:
[root@localhost ~]# echo "/^dracut/" >>/etc/urpmi/skip.list
[root@localhost ~]# nl -ba /etc/urpmi/skip.list
1 # Here you can specify the packages that won't be upgraded automatically
2 # for example, to exclude all apache packages :
3 # /^apache/
4
5 /^dracut/
Step 3: Network connectivity
Example: Check network configuration
[user@localhost ~]$ /usr/sbin/ifconfig
enp0s31f6: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether e4:e7:49:0a:04:8e txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
device interrupt 16 memory 0xde400000-de420000
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 2208 bytes 5724001 (5.4 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 2208 bytes 5724001 (5.4 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
wlp2s0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.1.114 netmask 255.255.255.0 broadcast 192.168.101.255
inet6 fe80::224:d6ff:fef5:b69e prefixlen 64 scopeid 0x20<link>
ether 00:24:d6:f5:b6:9e txqueuelen 1000 (Ethernet)
RX packets 348345 bytes 455328105 (434.2 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 179419 bytes 24441450 (23.3 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Note: This shows ethernet interface enp0s31f6 is not in use and has no IP address. Also, wireless interface wlp2s0 is configured and has IP address 192.168.1.114.
Example: verify network connectivity
[live@localhost ~]$ ping -c2 8.8.4.4 PING 8.8.4.4 (8.8.4.4) 56(84) bytes of data. 64 bytes from 8.8.4.4: icmp_seq=1 ttl=53 time=10.4 ms 64 bytes from 8.8.4.4: icmp_seq=2 ttl=53 time=10.8 ms --- 8.8.4.4 ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 3ms rtt min/avg/max/mdev = 10.361/10.593/10.826/0.254 ms
Note: Showing that 2 ICMP echo requests (ping) get responses from 8.8.4.4 (one of Google's public DNS servers).
Step 4: Configuring URPMI resources
Example: configure Mageia URPMI media sources to network only
/bin/su -c "/usr/sbin/urpmi.removemedia -a && /usr/sbin/urpmi.addmedia --distrib --mirrorlist"
[live@localhost ~]$ /bin/su -c "/usr/sbin/urpmi.removemedia -a && /usr/sbin/urpmi.addmedia --distrib --mirrorlist"
removing medium "Live Core"
removing medium "Live Nonfree"
adding medium "Core Release"
adding medium "Core Release Debug" (ignored by default)
adding medium "Core Updates"
adding medium "Core Updates Debug" (ignored by default)
adding medium "Core Updates Testing" (ignored by default)
adding medium "Core Updates Testing Debug" (ignored by default)
adding medium "Core Backports" (ignored by default)
adding medium "Core Backports Debug" (ignored by default)
adding medium "Core Backports Testing" (ignored by default)
adding medium "Core Backports Testing Debug" (ignored by default)
adding medium "Nonfree Release"
adding medium "Nonfree Release Debug" (ignored by default)
adding medium "Nonfree Updates"
adding medium "Nonfree Updates Debug" (ignored by default)
adding medium "Nonfree Updates Testing" (ignored by default)
adding medium "Nonfree Updates Testing Debug" (ignored by default)
adding medium "Nonfree Backports" (ignored by default)
adding medium "Nonfree Backports Debug" (ignored by default)
adding medium "Nonfree Backports Testing" (ignored by default)
adding medium "Nonfree Backports Testing Debug" (ignored by default)
adding medium "Tainted Release" (ignored by default)
adding medium "Tainted Release Debug" (ignored by default)
adding medium "Tainted Updates" (ignored by default)
adding medium "Tainted Updates Debug" (ignored by default)
adding medium "Tainted Updates Testing" (ignored by default)
adding medium "Tainted Updates Testing Debug" (ignored by default)
adding medium "Tainted Backports" (ignored by default)
adding medium "Tainted Backports Debug" (ignored by default)
adding medium "Tainted Backports Testing" (ignored by default)
adding medium "Tainted Backports Testing Debug" (ignored by default)
adding medium "Core 32bit Release" (ignored by default)
adding medium "Core 32bit Updates" (ignored by default)
adding medium "Core 32bit Updates Testing" (ignored by default)
adding medium "Core 32bit Backports" (ignored by default)
adding medium "Core 32bit Backports Testing" (ignored by default)
adding medium "Nonfree 32bit Release" (ignored by default)
adding medium "Nonfree 32bit Updates" (ignored by default)
adding medium "Nonfree 32bit Updates Testing" (ignored by default)
adding medium "Nonfree 32bit Backports" (ignored by default)
adding medium "Nonfree 32bit Backports Testing" (ignored by default)
adding medium "Tainted 32bit Release" (ignored by default)
adding medium "Tainted 32bit Updates" (ignored by default)
adding medium "Tainted 32bit Updates Testing" (ignored by default)
adding medium "Tainted 32bit Backports" (ignored by default)
adding medium "Tainted 32bit Backports Testing" (ignored by default)
$MIRRORLIST: media/core/release/media_info/20190627-235351-synthesis.hdlist.cz
$MIRRORLIST: media/core/updates/media_info/20191208-180358-synthesis.hdlist.cz
$MIRRORLIST: media/nonfree/release/media_info/20190628-001219-synthesis.hdlist.cz
$MIRRORLIST: media/nonfree/updates/media_info/20191119-211043-synthesis.hdlist.cz
Example: Verify Mageia URPMI sources configuration
Here we install a single package in order to check package installation is working correctly. In this case, we install package: tcptraceroute
/bin/su -c "/usr/sbin/urpmi tcptraceroute"
[live@localhost ~]$ /bin/su -c "/usr/sbin/urpmi tcptraceroute"
To satisfy dependencies, the following packages are going to be installed:
Package Version Release Arch
(medium "Core Release")
lib64net1 1.1.6 8.mga7 x86_64
tcptraceroute 1.5 1.beta7.11.m> x86_64
233KB of additional disk space will be used.
97KB of packages will be retrieved.
Proceed with the installation of the 2 packages? (Y/n) y
$MIRRORLIST: media/core/release/lib64net1-1.1.6-8.mga7.x86_64.rpm
$MIRRORLIST: media/core/release/tcptraceroute-1.5-1.beta7.11.mga7.x86_64.rpm
installing tcptraceroute-1.5-1.beta7.11.mga7.x86_64.rpm lib64net1-1.1.6-8.mga7.x86_64.rpm from /var/cache/urpmi/rpms
Preparing... ###################################################################################
1/2: lib64net1 ###################################################################################
2/2: tcptraceroute ###################################################################################
Example: apply pending updates
/usr/sbin/urpmi --auto-update
[live@localhost ~]$ /bin/su -c "/usr/sbin/urpmi --auto-update" medium "Core Release" is up-to-date medium "Core Updates" is up-to-date medium "Nonfree Release" is up-to-date medium "Nonfree Updates" is up-to-date Packages are up to date
Appendix-1: modified mgalive-root.sh with LUKS support
#!/usr/bin/sh
. /lib/dracut-lib.sh
can_decrypt=0
if [ -f /lib/dracut-crypt-lib.sh ] ; then
. /lib/dracut-crypt-lib.sh
can_decrypt=1
fi
[ -f /tmp/root.info ] && . /tmp/root.info
PATH=/usr/sbin:/usr/bin:/sbin:/bin
[ -z "$1" ] && exit 1
livedev="$1"
# Create the live tree
mkdir -m 0755 -p /live/distrib
mkdir -m 0755 -p /live/media
mkdir -m 0755 -p /live/overlay
mkdir -m 0755 -p /live/union
mkdir -m 0755 -p /run/mgalive/ovlsize
# Get the base device name
basedev=$(echo $livedev | sed -e 's,\(/dev/sd[a-z]\)1,\1,g' -e 's,\(/dev/mmcblk[0-9]\)p1,\1,g')
# Make it available to draklive-install and mgalive-shutdown
echo $basedev > /run/mgalive/basedev
# Unlock any encrypted partitions on the base device
if [ $can_decrypt -eq 1 ] ; then
for dev in $(blkid -t TYPE=crypto_LUKS -o device | grep $basedev) ; do
ask_for_password \
--ply-cmd "cryptsetup open -T1 $dev crypt_${dev##/dev/}" \
--ply-prompt "Password ($dev)" \
--ply-tries 3 \
--tty-cmd "cryptsetup open -T3 $dev crypt_${dev##/dev/}" \
--tty-tries 1
done
fi
# Get the base directory for locating the loopback file. In normal use this is
# the root directory, but a multi-boot USB stick may want to override this.
basedir=$(getarg mgalive.basedir)
# Get the device or path used for persistent storage (if it exists). In normal
# use this is another partition on the same base device, but a multi-boot USB
# stick may want to override this.
overlay=$(getarg mgalive.overlay)
if [ -z "$overlay" ] ; then
overlay=$(blkid -t LABEL=mgalive-persist -o device | grep $basedev'\|'/dev/mapper)
else
overlay=$livedev$overlay
fi
info "mgalive basedev is $basedev"
info "mgalive livedev is $livedev"
info "mgalive basedir is $basedir/"
info "mgalive overlay is $overlay"
media=$livedev
if [ -z "$(blkid $livedev)" ] ; then
if strstr "$(blkid $basedev)" "iso9660" ; then
# This happens when we boot from a USB stick with a isohybrid partition
# scheme where the first sector is unclaimed, so the first partition starts
# at sector 1. The iso9660 filesystem starts at sector 0, so blkid doesn't
# detect a valid filesystem in the first partition. udev, however, links
# the entry in /dev/disk/by-label to the first partition, not to the raw
# device, and that is what we get passed in $1 (mga#3334).
if [ -n "$overlay" ] ; then
# If we mount the raw device, we can't then also mount a partition
# on that device. So to enable persistence, we need to extend the
# first partition to claim the full range of the iso9660 filesystem.
ps=$(partx -go START $livedev)
pe=$(partx -go END $livedev)
if [ $ps -eq 1 ] ; then
info "Extending $livedev to cover sector 0"
delpart $basedev 1
addpart $basedev 1 0 $pe
else
info "$livedev is not a valid protective partition"
fi
else
# If we don't have a persistent partition, take the easy option.
info "Using $basedev to mount the iso9660 filesystem"
media=$basedev
fi
else
info "$livedev does not contain a valid filesystem"
fi
fi
# Mount the live media
mount -n -o ro $media /live/media
# Mount the loopback filesystem
LOOPDEV=$( losetup -f )
if [ -e /live/media$basedir/loopbacks/distrib-lzma.sqfs ] ; then
# Retain support for the original draklive. Note that despite the file
# name, it uses xz compression.
losetup -r $LOOPDEV /live/media$basedir/loopbacks/distrib-lzma.sqfs
else
losetup -r $LOOPDEV /live/media$basedir/loopbacks/distrib.sqfs
fi
mount -n -t squashfs -o ro $LOOPDEV /live/distrib
mount -n -t squashfs -o ro $LOOPDEV /run/mgalive/ovlsize
# Mount the overlay filesystem
if [ -z "$overlay" ] ; then
mount -n -t tmpfs -o mode=755 none /live/overlay
else
mount -n -o noatime $overlay /live/overlay
echo 1 > /run/mgalive/persistent
fi
# work and memory must be on same root
mkdir -m 0755 -p /live/overlay/work
mkdir -m 0755 -p /live/overlay/memory
mount -n -t overlay overlay -o lowerdir=/live/distrib,upperdir=/live/overlay/memory,workdir=/live/overlay/work,noatime /live/union
ln -s /live/union /dev/root
printf '/bin/mount --rbind /live/union %s\n' "$NEWROOT" > $hookdir/mount/01-$$-live.sh
printf '/bin/umount /live/union\n' >> $hookdir/mount/01-$$-live.sh
# /live will not be visible once we pivot, so schedule its cleanup now.
# This is needed to allow a persistent overlay to be shutdown cleanly.
umount -l /live/distrib
umount -l /live/overlay
umount -l /live/media
need_shutdown
exit 0